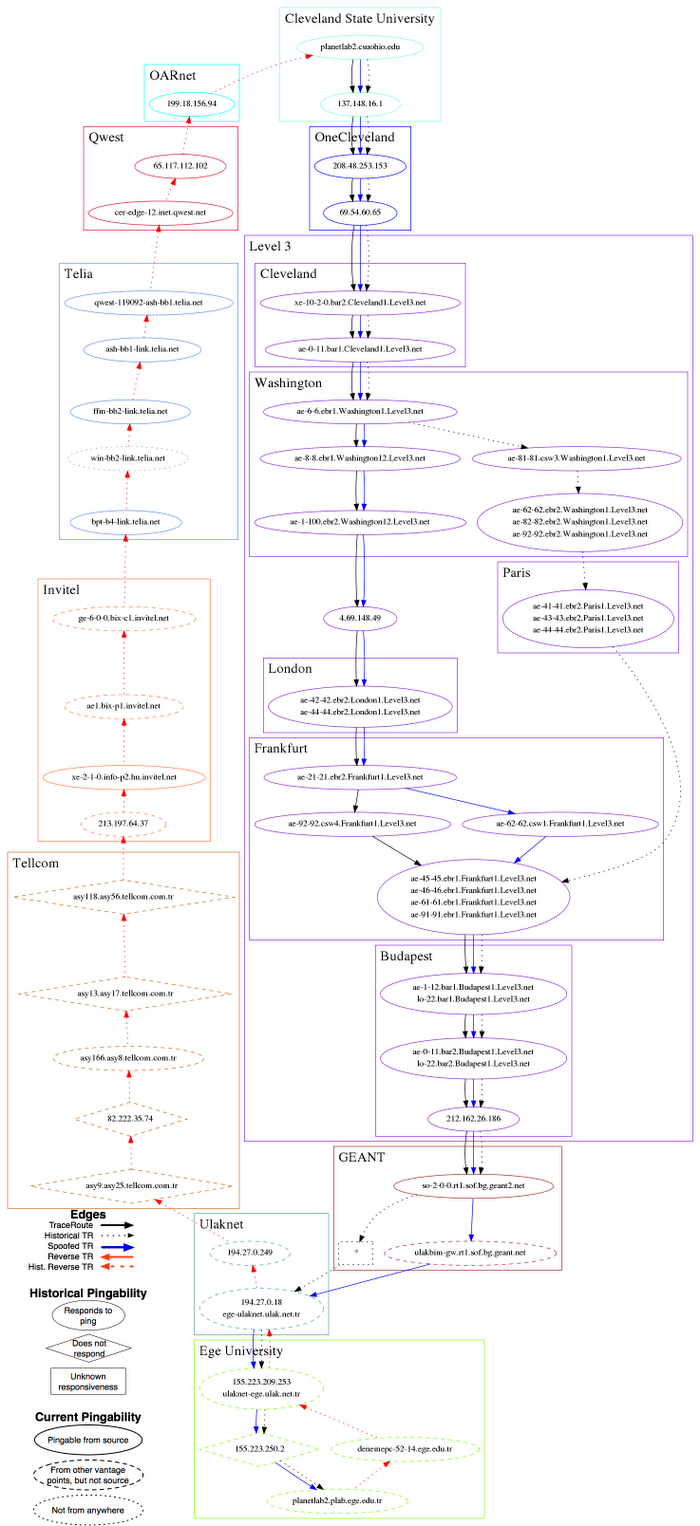
One of LIFEGUARD's vantage points is planetlab2.csohio.edu, a PlanetLab host at Cleveland State University. According to LIFEGUARD's historical record, routes between that vantage point and planetlab2.plab.ege.edu.tr (a PlanetLab host at Ege University in Turkey) had been asymmetric: the forward path used OneCleveland, Level3, Geant and Ulak, whereas the reverse path started with Ulak but then diverged from the forward path and used Tellcom, Invitel, Telia and Qwest.
When the Cleveland State source detected a problem, it sent a traceroute to the Turkish PlanetLab host. The last responsive hop on the traceroute was in GEANT. The Turkish university was still reachable from other LIFEGUARD vantage points, including planetlab1.sfc.wide.ad.jp, a PlanetLab host in Japan. To isolate the forward path from the reverse path, LIFEGUARD had the Cleveland State source send a traceroute to Ege University, spoofing as the Japanese PlanetLab host. These probes measured the complete forward path, revealing that the path through Ulak was indeed still working in the forward direction -- information unavailable from non-spoofed traceroute measurements. In contrast, probes from Japan spoofing as Cleveland State failed. With these measurements, LIFEGUARD isolated the direction of the outage to the reverse path (Ege University to Cleveland State).
The source then issued pings to hops along the historical reverse paths to identify which routers still had working paths to the source. It received responses from hops in Invitel, Telia, and Qwest, but not from hops in Ulak or Tellcom. These results placed the "reachability horizon" at a router on the border between Invitel and Tellcom (router IP 213.197.64.37, owned by Invitel according to whois) because it was the first unresponsive router beyond the farthest reverse-path hop reachable from the source.
The following image (click the image for the full-size version) displays the measurements that LIFEGUARD issued.
|